Virtual Data Room Checklist: What should be in your VDR
The Essential Virtual Data Room Setup Checklist
Setting up a virtual data room (VDR) is a critical step in many business processes — from M&A transactions and fundraising to legal proceedings and strategic partnerships. But how do you ensure your VDR is properly configured for maximum security, efficiency, and compliance?
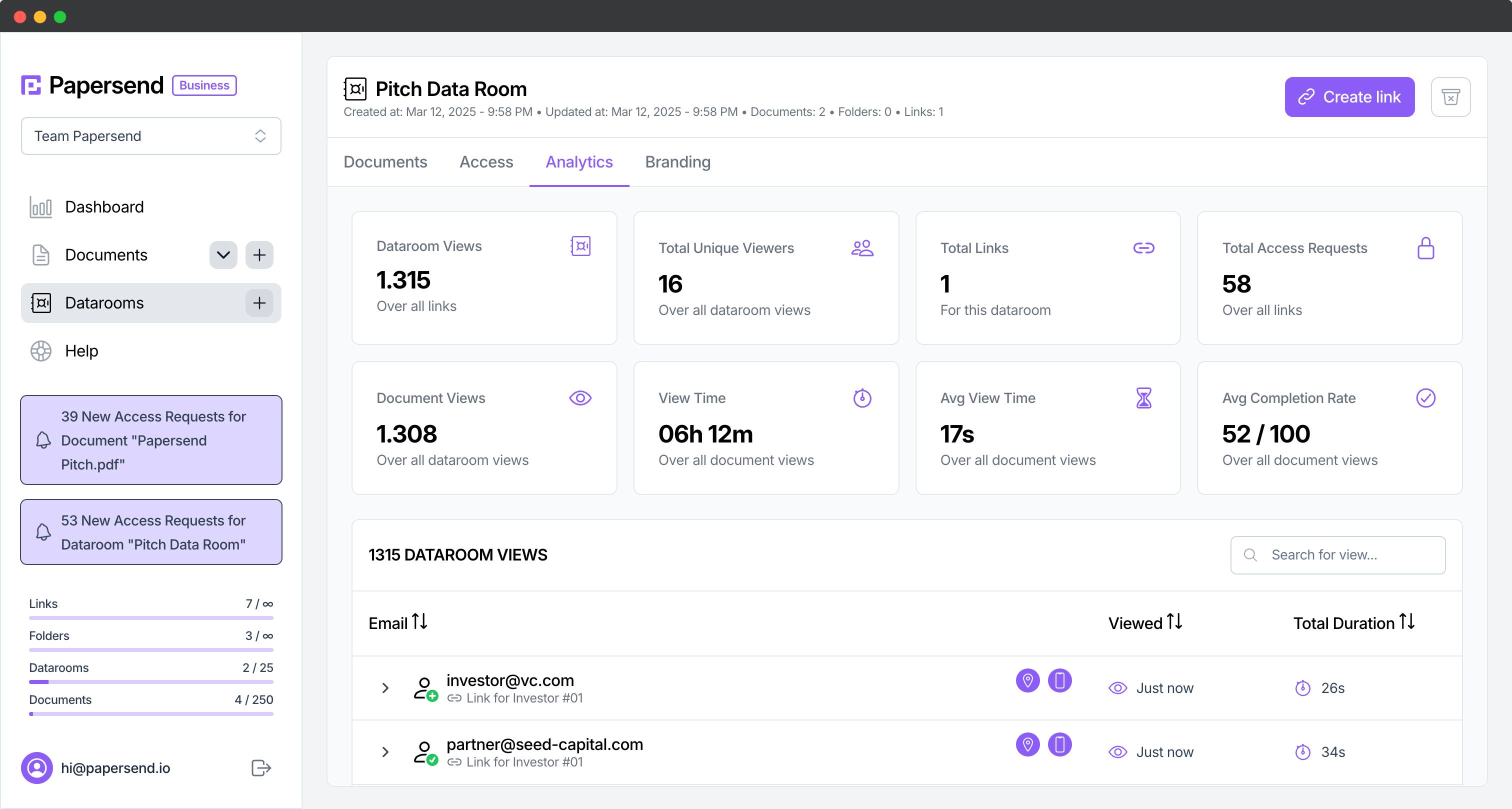
This comprehensive checklist covers everything you need to know about configuring and managing a secure virtual data room. Whether you’re preparing for due diligence, organizing sensitive documents for investors, or establishing a centralized repository for confidential information, this guide will help you set up a robust VDR that protects your most sensitive data.
What is a Virtual Data Room?
A virtual data room (VDR) is a secure online repository used to store, share, and review confidential documents. Think of it as a highly secure digital filing cabinet with advanced protection measures and tracking capabilities.
Unlike general file-sharing platforms, VDRs are designed specifically for handling sensitive business information with robust security features including:
- End-to-end encryption
- Granular permission controls
- Comprehensive audit logs
- Document watermarking
- Viewer activity tracking
- Time-limited access
According to a 2024 report from Grand View Research, the global virtual data room market is projected to grow at a CAGR of 14.5% from 2024 to 2030, highlighting the increasing demand for secure document sharing solutions.
Pre-Setup Planning
Before diving into the technical setup of your VDR, take time to plan strategically:
Define Your Objectives
Identify your primary use case
- M&A transactions
- Fundraising
- Due diligence
- Legal proceedings
- Board communications
- Regulatory compliance
Establish timeline requirements
- Project duration
- Key milestones
- Access expiration dates
Determine stakeholder roles
- Internal administrators
- External reviewers
- Document owners
- Compliance officers
Document Inventory Assessment
Before uploading files, create an inventory of all documents that will be included:
| Document Category | Examples | Sensitivity Level |
|---|---|---|
| Financial Records | Balance sheets, P&L statements, Tax returns | High |
| Legal Documents | Contracts, IP registrations, Litigation records | High |
| Corporate Records | Board minutes, Shareholder agreements | Medium-High |
| Operational Documents | Processes, Policies, Procedures | Medium |
| HR Documents | Employment contracts, Organization charts | High |
| Marketing Materials | Product sheets, Market analyses | Low-Medium |
Security Configuration Checklist
Security is the foundation of an effective virtual data room. Here’s a comprehensive checklist to ensure your VDR maintains the highest level of protection:
Encryption and Access Security
Implement end-to-end encryption
- Ensure data is encrypted at rest and in transit
- Verify SSL/TLS implementation for all connections
Configure multi-factor authentication (MFA)
- Require MFA for all administrator accounts
- Enable MFA options for all users
Set up IP restrictions
- Limit access to approved IP addresses when possible
- Create geographic access restrictions if needed
Establish secure password policies
- Require strong passwords with minimum complexity requirements
- Implement password expiration and history policies
Document Protection Measures
Enable dynamic watermarking
- Configure watermarks to display user information
- Include date/time stamps on viewed documents
Set document permissions
- View-only access for sensitive documents
- Disable download, print, and copy functions
- Prevent screenshots where applicable
Configure document expiration
- Set time-limited access for external users
- Implement automatic document expiration dates
Enable document-level encryption
- Apply additional encryption to highly sensitive files
- Implement separate access keys for critical documents
Organizational Structure Setup
A well-organized VDR improves efficiency and ensures users can quickly find the information they need:
Folder Structure Best Practices
Create a logical, intuitive folder structure that anticipates how users will navigate the information:
Implement a standardized naming convention
- Use clear, descriptive folder names
- Include dates in standardized format when relevant
- Create a documented naming policy for consistency
Design a hierarchical structure
- Organize from general to specific
- Limit folder depth to 3-4 levels when possible
- Group related documents logically
Create dedicated sections by function
- Financial information
- Legal documents
- Operational records
- HR documentation
- Marketing materials
Include index documents
- Add README files in key folders explaining contents
- Provide navigation guides for complex sections
Document Versioning Strategy
Establish version control protocols
- Determine whether to maintain multiple versions or replace
- Create a version naming convention (v1.0, v1.1, etc.)
Set up document replacement rules
- Define when to replace vs. add new versions
- Configure automatic versioning when possible
Create document change logs
- Maintain records of document updates
- Include reasons for document revisions
User Permission Setup
Granular user permissions are essential for maintaining control over your sensitive information:
User Group Configuration
Create role-based user groups
- Administrators with full control
- Internal team members with edit rights
- External reviewers with limited access
- Auditors with specialized permissions
Implement permission inheritance
- Set top-level permissions that cascade
- Override inheritance for special cases
Configure group-level restrictions
- Apply bulk permissions by department or function
- Create templates for common user types
Individual User Permissions
Set granular document access
- Configure permissions at folder and file levels
- Restrict view, download, print, and share capabilities
Establish time-limited access
- Set expiration dates for external users
- Configure automatic deactivation triggers
Implement view tracking
- Enable notifications for document access
- Track time spent on each document
Compliance and Audit Trail Configuration
Robust compliance controls and comprehensive audit trails are essential for regulatory requirements and internal governance:
Regulatory Compliance Setup
Configure industry-specific compliance features
- GDPR settings for European data
- HIPAA controls for healthcare information
- SOX requirements for financial documents
- FINRA compliance for financial services
Set up data residency controls
- Select appropriate server locations
- Implement geographic restrictions
Establish retention policies
- Configure document retention timeframes
- Set up automatic archiving or deletion
Audit Trail Implementation
Activate comprehensive logging
- Track all user actions (view, download, print)
- Log administrator activities
- Record permission changes
Configure audit reports
- Set up scheduled activity reports
- Create custom reporting templates
- Establish distribution lists for reports
Enable real-time notifications
- Alert administrators to unusual activity
- Notify document owners of access events
According to a PwC Global Digital Trust Insights survey, organizations with robust monitoring and audit capabilities detect breaches 33% faster than those without, significantly reducing potential damages.
Data Room Launch Preparation
Before making your VDR accessible to users, complete these final preparation steps:
Pre-Launch Testing
Conduct a thorough security review
- Test all security measures from external locations
- Verify encryption implementation
- Check for permission gaps
Perform user acceptance testing
- Test access with sample users from each group
- Verify all documents display correctly
- Confirm watermarking and protection features
Check system performance
- Test with peak expected user loads
- Verify document loading times
- Confirm notifications are working properly
User Onboarding Plan
Create user guides and documentation
- Develop role-specific quick start guides
- Produce video tutorials for common tasks
- Create FAQ documents for self-service support
Establish support processes
- Configure help desk access
- Set up escalation procedures
- Create troubleshooting documentation
Schedule training sessions
- Plan administrator training
- Organize user orientation webinars
- Create a timeline for rollout
Ongoing Management Best Practices
Once your VDR is operational, implement these management practices to ensure continued security and efficiency:
Regular Maintenance Procedures
Conduct periodic security reviews
- Schedule monthly permission audits
- Review unusual access patterns
- Update security settings as needed
Maintain document relevance
- Archive outdated materials
- Update documents with new versions
- Remove unnecessary files
Monitor system performance
- Track loading times and user experience
- Address performance issues promptly
- Schedule maintenance during off-peak hours
Communication Management
Establish Q&A procedures
- Set up Q&A sections within the data room
- Create clear processes for addressing questions
- Define response time expectations
Implement notification protocols
- Configure updates for document additions
- Set alert thresholds for security events
- Establish communication channels for issues
Industry-Specific VDR Considerations
Different industries have unique requirements for their virtual data rooms:
M&A Transactions
For merger and acquisition processes, consider these specialized configurations:
Implement staged disclosure
- Create multiple data room phases with progressive access
- Use NDAs to control information flow
- Configure “clean rooms” for highly sensitive competitive information
Set up buyer comparison tools
- Enable side-by-side tracking of multiple bidders
- Configure activity reports by buyer group
- Implement Q&A management by potential acquirer
Investment and Fundraising
For startups and companies raising capital:
Create investor-friendly navigation
- Organize documents according to standard fundraising categories
- Include executive summaries at top levels
- Structure financial information progressively
Implement engagement analytics
- Track which investors spend time on which documents
- Set up alerts for high-value investor activity
- Configure follow-up reminders based on engagement
Legal Proceedings
For law firms and legal departments:
Set up matter-specific organization
- Organize by case or matter number
- Implement legal hold notifications
- Configure privilege protection markers
Enable secure external counsel access
- Create specialized permission groups for external legal teams
- Implement ethical walls between case teams
- Configure evidence chain of custody tracking
Data Room Security Best Practices
Beyond basic setup, these advanced security practices will further protect your sensitive information:
Advanced Protection Measures
Implement digital rights management (DRM)
- Apply persistent protection to downloaded documents
- Enable remote revocation of access
- Set up automatic document expiration
Configure device management
- Limit access to approved devices
- Set up device verification protocols
- Implement automated device timeouts
Security Administration
Establish security monitoring protocols
- Set up regular security reviews
- Create incident response procedures
- Implement automated threat detection
Configure backup and recovery processes
- Set up automated data backups
- Establish recovery time objectives
- Test restoration procedures regularly
VDR Provider Selection Criteria
If you’re still evaluating VDR providers, consider these key factors:
| Feature Category | Important Considerations | Why It Matters |
|---|---|---|
| Security | Encryption standards, access controls, certifications | Protects sensitive data from unauthorized access |
| Ease of Use | Interface design, mobile accessibility, setup time | Ensures adoption and efficient use |
| Permission Controls | Granularity of permissions, group settings, view restrictions | Maintains precise control over who sees what |
| Document Features | Watermarking, version control, format support | Enhances document protection and management |
| Activity Tracking | User logs, document analytics, real-time notifications | Provides insights into user engagement |
| Support | 24/7 availability, training options, response time | Ensures smooth operation and issue resolution |
| Compliance | Industry-specific certifications, geographic data controls | Meets regulatory requirements |
| Pricing Structure | Per-page vs. flat-rate, storage limits, user licensing | Affects total cost of ownership |
Conclusion: Your VDR Success Checklist
A well-configured virtual data room is essential for secure document sharing and streamlined due diligence processes. By following this comprehensive checklist, you can ensure your VDR provides maximum security, efficiency, and compliance.
Key takeaways for VDR success:
- Security first: Implement robust encryption, access controls, and document protection
- Intuitive organization: Create a logical structure that makes information easy to find
- Granular permissions: Configure precise access controls for different user types
- Comprehensive monitoring: Track all activity with detailed audit trails
- Regular maintenance: Keep security settings and document libraries up to date
Ready to set up your secure, efficient virtual data room?
Frequently Asked Questions
A Virtual Data Room (VDR) is a secure online repository for storing and sharing confidential documents, offering advanced protection measures like encryption, permission controls, and audit logs. It's critical for secure business processes like M&A, fundraising, and legal proceedings, ensuring data security and compliance.
The key steps include defining objectives (like use case and timeline), assessing document inventory, configuring security (encryption, MFA, watermarking), setting up an organized folder structure, managing user permissions, ensuring compliance, conducting pre-launch testing, and establishing ongoing maintenance procedures.
Ensure document security by implementing end-to-end encryption, configuring multi-factor authentication (MFA), setting up IP restrictions, enabling dynamic watermarking, setting granular document permissions (view-only, disabling download/print), configuring document expiration, and enabling document-level encryption.
Follow best practices like implementing a standardized naming convention, designing a hierarchical structure (general to specific), creating dedicated sections by function (financial, legal, HR), and including index documents. Also, establish version control protocols and document change logs for effective document management.
Maintain compliance by configuring industry-specific features (GDPR, HIPAA, SOX), setting up data residency controls, and establishing retention policies. Implement audit trails by activating comprehensive logging of user actions, configuring audit reports, and enabling real-time notifications for unusual activity.