8 Ways to Prevent PDF Forwarding in 2025
How to Prevent Unauthorized PDF Forwarding
Have you ever shared a confidential PDF only to worry about where it might end up? Whether it’s business proposals, financial statements, or intellectual property, preventing unauthorized forwarding is crucial for maintaining document security and compliance.
In this comprehensive guide, we’ll explore proven strategies to secure your PDFs and prevent them from being forwarded without your permission. You’ll learn about both traditional methods and advanced solutions that give you complete control over your sensitive documents.
Why Document Security Matters
Before diving into specific protection methods, let’s understand why preventing unauthorized PDF forwarding is so critical:
The Risks of Unsecured Document Sharing
When sensitive PDFs are shared without proper protection:
- Confidential information can reach competitors or unauthorized parties
- Intellectual property may be compromised
- Compliance violations can occur (GDPR, HIPAA, etc.)
- Business reputation might suffer from data breaches
- Client trust can be permanently damaged
Most organizations still rely on outdated document security measures that don’t address modern sharing challenges. Traditional methods like simple password protection don’t prevent recipients from forwarding documents to unauthorized parties.
8 Effective Methods to Prevent PDF Forwarding
Let’s explore the most effective strategies to prevent unauthorized PDF forwarding, from basic approaches to advanced security measures.
1. Password Protection
Password protection is the most basic security measure but still serves as a useful first line of defense.
How to implement password protection:
Using Adobe Acrobat Pro:
- Open your PDF
- Go to “Tools” > “Protect” > “Encrypt” > “Encrypt with Password”
- Set permissions to restrict editing and printing
Using Online Tools:
Limitations: While password protection restricts access, it doesn’t prevent authorized users from forwarding the password along with the document.
2. Document Encryption
Encryption transforms your PDF content into an unreadable format without the proper decryption key, providing a stronger layer of security than simple password protection.
Benefits of encryption:
- Makes content completely unreadable without the encryption key
- Protects document integrity during transmission
- Complies with regulatory requirements for data protection
Industry-standard encryption methods:
- AES (Advanced Encryption Standard) 256-bit encryption
- RSA encryption for key exchange
3. Allow/Block Lists of Viewers
Creating specified lists of authorized viewers enables granular access control.
How it works:
- Define allowed email addresses/accounts that can access the document
- Block specific domains or users from accessing sensitive content
- Receive alerts when unauthorized access attempts occur
4. Digital Watermarking
Watermarking embeds visible or invisible information into your PDF that identifies its origin or authorized recipient.
Types of watermarks:
- Visible watermarks: Company logos, “Confidential” labels, or recipient’s email/name
- Invisible watermarks: Hidden identifiers that can trace leaked documents back to the source
Benefits:
- Deters unauthorized sharing by making the recipient identifiable
- Helps trace the source of leaks if documents are shared improperly
- Maintains document integrity while adding a layer of accountability
5. Convert PDF to Image Format
Converting a PDF to image format (JPEG, PNG) makes the content more difficult to extract or edit, adding a practical barrier to misuse.
Pros:
- Prevents easy text extraction
- Makes document manipulation more challenging
- Maintains visual appearance of the original document
Cons:
- Increases file size
- Reduces text searchability
- May decrease image quality
Recommended tools:
6. Share as a Secure Link
How it works:
- Upload your PDF to a secure document-sharing platform
- Generate a secure link with custom access settings
- Share the link with your intended recipients
- Monitor access and revoke permissions when needed
Key benefits:
- Maintain control over the document even after sharing
- Set link expiration dates
- Track who views the document and for how long
- Revoke access instantly if needed
- Upload Your PDF
- Log in to Papersend
- Upload your PDF document. Did you know? Papersend supports over 160 different file types.
- Organize in folders if needed
- Configure Access Settings
- Set to “view-only” to prevent downloads
- Provide an Allow/Block List for granular viewer access
- Set expiration date or view limits
- Generate and Share Your Secure Link
- Create a trackable link
- Enable notifications for views
- Share via email, messaging, or your preferred platform
- Monitor Document Activity
- Track who accessed your document
- See viewing duration and engagement
- Receive notifications of access attempts
7. Digital Rights Management (DRM)
DRM technology provides comprehensive control over how users interact with your PDFs.
What DRM allows you to control:
- Viewing permissions
- Printing restrictions
- Copy/paste functionality
- Editing capabilities
- Download options
- Forwarding prevention
Enterprise DRM solutions:
8. Use Secure Document Sharing Platforms
Purpose-built secure document sharing platforms like Papersend combine multiple security features into an integrated solution.
Key features to look for:
- End-to-end encryption
- Granular access controls
- View-only options
- Watermarking capabilities
- Access expiration settings
- Comprehensive tracking analytics
- Revocation capabilities
Advanced PDF Protection with Papersend
Papersend offers a comprehensive solution for preventing unauthorized PDF forwarding with features specifically designed for maximum security with minimal friction.
Complete Control Over Your Documents
With Papersend, you can:
| Feature | How It Helps |
|---|---|
| Access Controls | Set precise permissions for who can view your documents |
| View-Only Mode | Prevent downloads while allowing viewing |
| Custom Expiry | Set documents to become inaccessible after a specific date |
| Access Revocation | Instantly remove access regardless of who has the link |
| View Tracking | Monitor exactly who viewed your document and for how long |
| Device Restrictions | Limit access to specific devices or locations |
| Email Verification | Ensure only authorized email addresses can access content |
| Email Confirmation | Ensure that only confirmed email addresses can access content. |
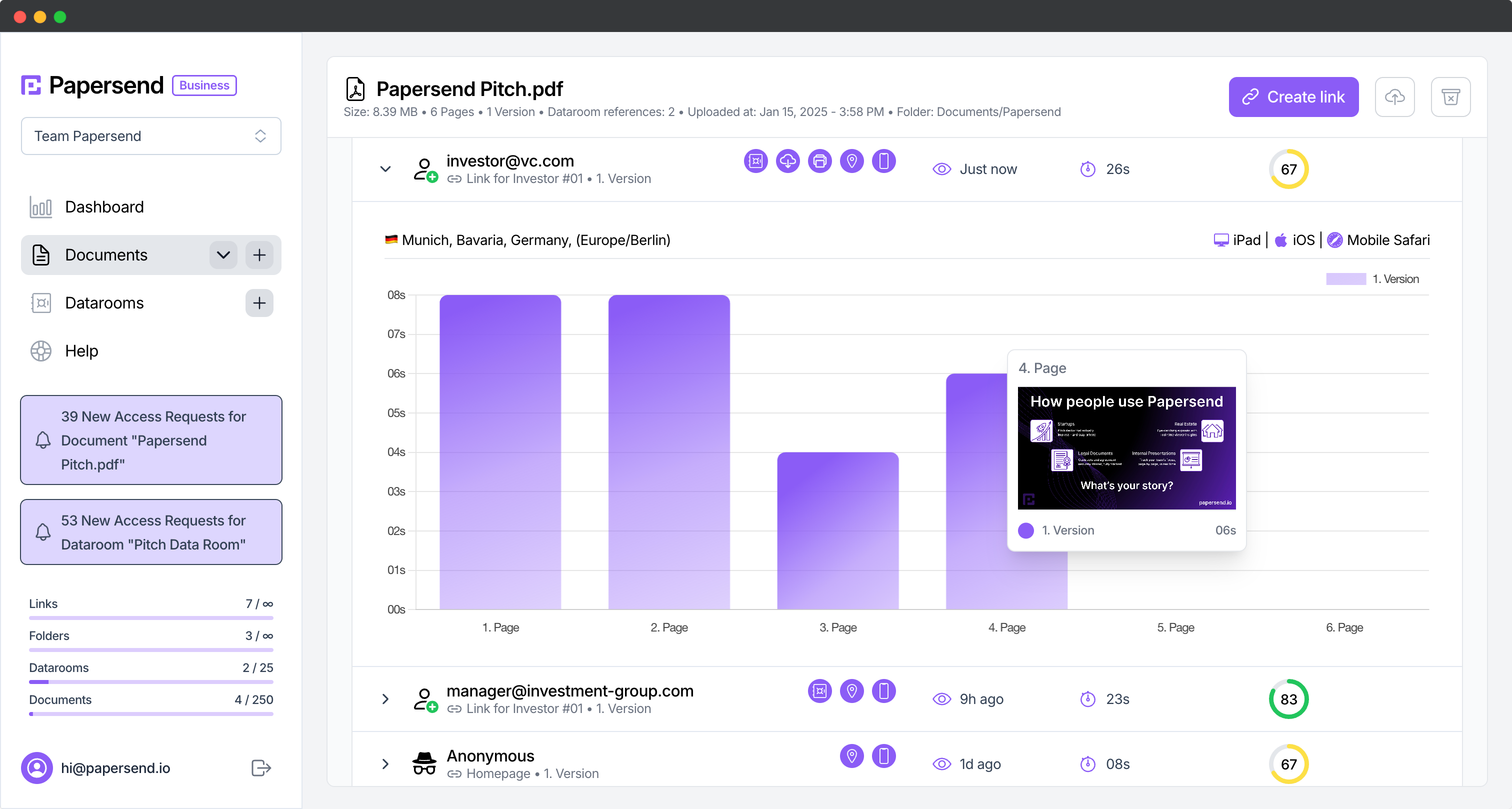
Real-time Analytics and Notifications
Know exactly what happens to your PDFs after you share them:
- Receive instant notifications when documents are viewed
- Track viewing time per page to gauge reader engagement
- See which devices and browsers accessed your document
- Monitor access attempts, including unauthorized tries
- Generate comprehensive access reports for compliance
Best Practices for Secure Document Sharing
Beyond implementing technical solutions, these best practices will enhance your document security:
1. Implement a Document Classification System
Categorize documents based on sensitivity levels to determine appropriate security measures:
- Public: No restrictions needed
- Internal: Basic access controls for team members only
- Confidential: Strong security with tracking and watermarking
- Highly Confidential: Maximum security with all available protections
2. Educate Your Team
Ensure everyone understands document security protocols:
- Provide training on secure sharing practices
- Establish clear policies for handling sensitive documents
- Create guidelines for determining document sensitivity levels
- Review security procedures regularly
3. Use Secure Communication Channels
How you share access information matters:
- Send document links and passwords through different channels
- Use encrypted communication tools for sharing sensitive access details
- Avoid sharing access information in public or unsecured environments
4. Regular Security Audits
Periodically review your document security:
- Check access logs for unusual patterns
- Review who has access to what documents
- Update or revoke access as team members change roles
- Test security measures to ensure they’re working properly
5. Have a Response Plan for Breaches
Prepare for potential security incidents:
- Create a clear protocol for handling unauthorized access
- Establish a communication plan for notifying affected parties
- Document steps for containing potential damage
- Learn from incidents to improve future security measures
Industry-Specific PDF Security Considerations
Different industries have unique document security needs and regulatory requirements:
Legal Industry
Law firms handle highly confidential client information that requires stringent protection:
- Client-attorney privileged communications
- Case strategy documents
- Settlement agreements
- Contracts and legal opinions
Healthcare
Healthcare organizations must comply with HIPAA and protect sensitive patient information:
- Patient records
- Treatment plans
- Research data
- Insurance information
Financial Services
Financial institutions handle sensitive client and proprietary data:
- Investment strategies
- Client financial records
- Internal financial projections
- Trading algorithms and models
Custom Domain Integration for Brand Consistency
When sharing secure documents, maintaining brand consistency builds trust with recipients.
Benefits include:
- Increased recipient trust
- Professional appearance
- Reinforced brand identity
- Reduced recipient confusion
Conclusion: Balancing Security and Accessibility
Preventing unauthorized PDF forwarding is essential for protecting sensitive information, but security shouldn’t come at the expense of usability. The most effective approach combines:
- Strong technical protections that prevent forwarding and unauthorized access
- User-friendly sharing processes that don’t create friction for legitimate recipients
- Comprehensive analytics that provide visibility into document usage
- Flexible control options that adapt to different security needs
By implementing the strategies outlined in this guide, you can ensure your sensitive PDFs remain secure while still being accessible to authorized viewers.
Ready to take control of your PDF security?
Frequently Asked Questions
Preventing unauthorized PDF forwarding is crucial because it safeguards confidential information from reaching competitors or unauthorized parties, protects intellectual property, avoids compliance violations (like GDPR, HIPAA), prevents damage to business reputation from data breaches, and maintains client trust.
Effective methods include password protection, document encryption, using allow/block lists of viewers, digital watermarking, converting PDFs to image formats, sharing as a secure link (with Papersend), implementing Digital Rights Management (DRM), and using secure document sharing platforms like Papersend.
Password protection is a basic security measure that restricts initial access to a PDF. However, its main limitation is that it doesn’t prevent authorized users from forwarding the password along with the document, potentially granting unauthorized access to others.
DRM technology provides comprehensive control over how users interact with PDFs, allowing you to control viewing permissions, printing restrictions, copy/paste functionality, editing capabilities, download options, and forwarding prevention, thus offering a robust method to secure sensitive documents.
Secure document sharing platforms like Papersend combine multiple security features, such as end-to-end encryption, granular access controls, view-only options, watermarking, access expiration settings, comprehensive tracking analytics, and revocation capabilities, into an integrated solution that maximizes security while minimizing friction.