Intellectual Property Leakage: Tactics to Secure Your Innovations
Understanding the Unseen Threat of Intellectual Property Leakage
The stakes of intellectual property (IP) protection have never been higher. While external attacks grab headlines, the real danger often arises subtly from within - the gradual, sometimes unintentional, escape of your most valuable innovations. Understanding and preventing this intellectual property leakage is critical for survival and growth.
Safeguarding your innovations requires more than just firewalls; it demands vigilance against the myriad ways sensitive information can slip through the cracks.
Defining Intellectual Property Leakage
Intellectual property leakage occurs when valuable IP assets—trade secrets, proprietary formulas, source code, business strategies—leave an organization’s control without authorization. Unlike obvious theft, IP leakage often happens gradually, sometimes unintentionally, posing a significant risk to businesses of all sizes. It’s the slow drip of information that can erode competitive advantage over time.
Types of Intellectual Property Vulnerabilities
Different types of IP face unique threats. Patents, trademarks, copyrights, and trade secrets all require specific protective measures in the digital age.
Code leakage is particularly devastating for tech companies. When proprietary source code escapes secure environments, competitors gain insights into core technology, potentially nullifying years of R&D investment. This often occurs via insider threats, compromised accounts, or insecure repositories.
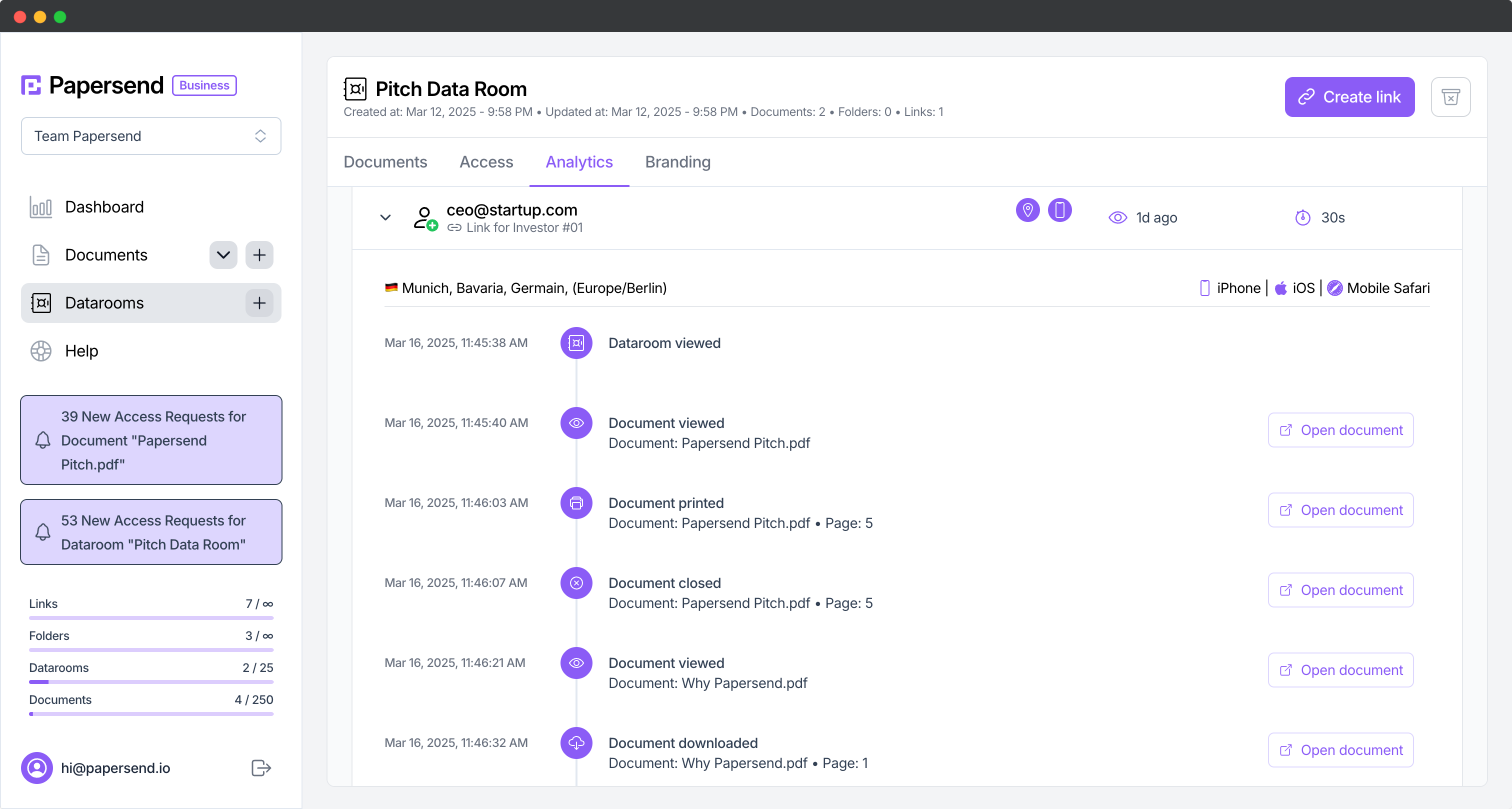
Trade secrets, like manufacturing processes or customer lists, are vulnerable to both internal and external actors. Unlike patents, once a trade secret is public, its protection is permanently lost. Preventing intellectual property loss is especially critical for information valued for its confidentiality. Robust document access control is vital here.
The Impact of IP Breaches on Business
IP breaches extend far beyond financial damage, impacting market position, customer trust, and competitive edge. Consequences include:
- Erosion of market share as competitors leverage stolen innovations.
- Damaged client relationships due to security concerns.
- Diminished company valuation affecting investment and acquisitions.
- Significant legal costs for recovery and remediation.
For startups, a single major IP breach can be catastrophic. Even large enterprises face destabilization from the loss of critical designs or algorithms. Recognizing these risks is the first step toward implementing effective intellectual property cyber security measures.
Common Causes and Risk Factors
IP leakage often results from a combination of vulnerabilities rather than a single event. Understanding these risk factors is key to effective protection.
Internal Threats
A significant portion of IP loss originates internally. Common scenarios include:
- Departing employees taking proprietary data, intentionally or not.
- Careless handling of sensitive documents by untrained staff.
- Deliberate theft by disgruntled employees.
- Insufficient vetting or oversight of contractors.
Digital Vulnerabilities
The shift to digital operations creates new avenues for IP breaches:
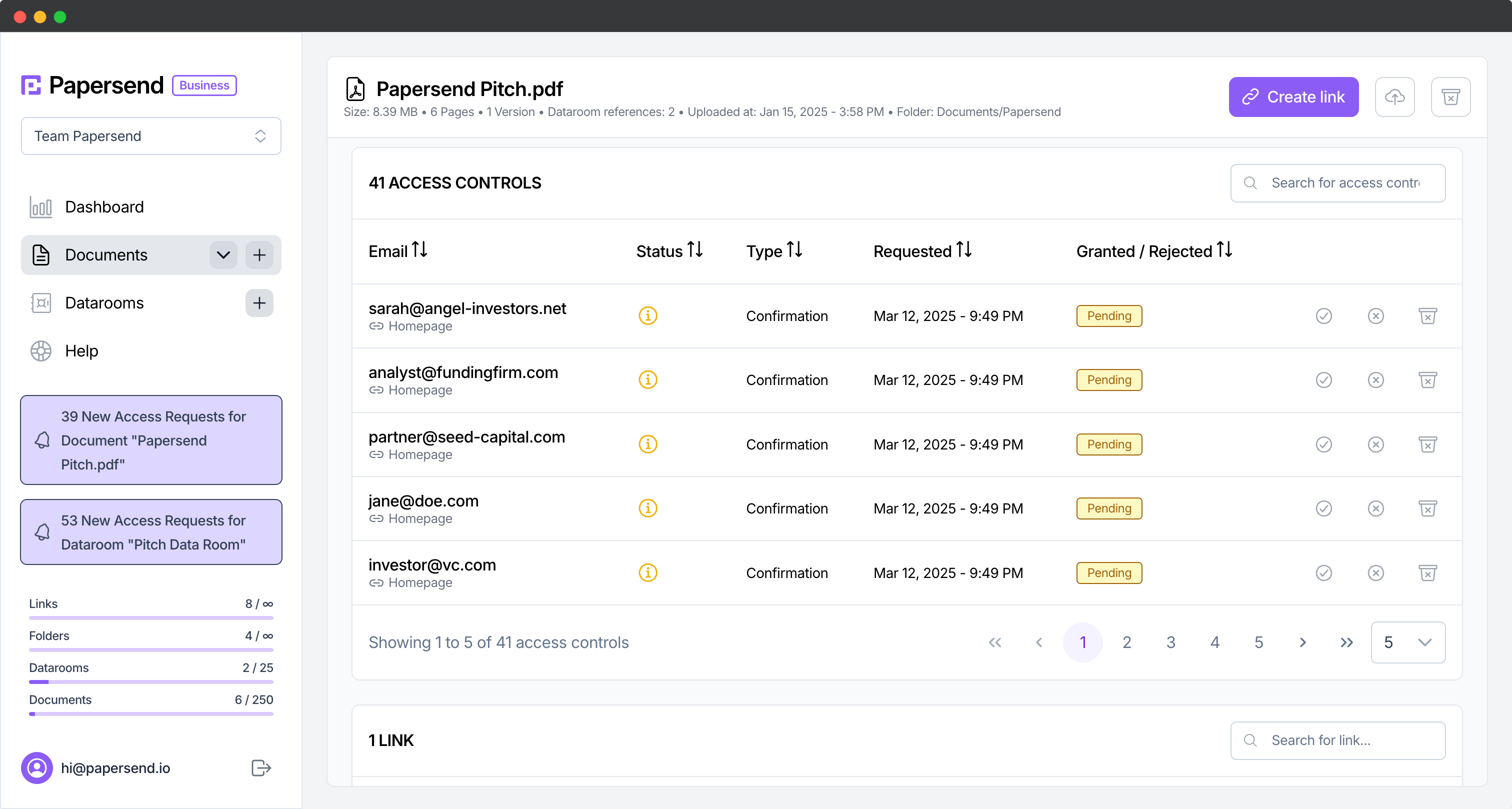
- Unsecured development environments lacking code protection.
- Weak access controls failing to limit sensitive data exposure. Explore Papersend’s access control features.
- Malware and phishing attacks targeting employees with IP access.
- Unpatched software and systems with known security flaws.
- Improperly configured cloud storage exposing confidential files.
Third-Party Exposure
IP often flows through partners, vendors, and clients, creating potential leak points:
- Sharing designs with manufacturers.
- Providing API access to tech partners.
- Outsourcing development work.
- Demonstrating confidential features to prospects.
Insufficient Legal Protection
Inadequate legal documentation is a surprising risk factor:
- Failure to document innovation ownership clearly.
- Lack of comprehensive non-disclosure agreements (NDAs).
- Delayed registration of patents, trademarks, and copyrights.
- Absence of clear IP policies for employees and contractors.
These oversights create ambiguity, potentially allowing others to exploit your innovations. A solid legal foundation is critical for all other security measures.
Real-World Cases and Impact Analysis
Examining real IP theft cases reveals common methods and devastating consequences, reinforcing the need for proactive protection.
High-Profile IP Breaches
Even industry leaders face breaches. The Uber/Waymo case, involving alleged theft of self-driving tech secrets by a former employee, resulted in a ~$245 million settlement, showcasing the high stakes. Another case involved an Apple employee charged with stealing autonomous vehicle secrets before joining a competitor, highlighting the departing employee vulnerability.
These examples show intellectual property theft meaning goes beyond copying; it’s the unauthorized transfer of R&D and competitive advantage.
Financial and Competitive Impact
IP theft leads to:
- Market value decline upon public disclosure.
- Long-term revenue loss as competitors exploit stolen IP.
- Substantial legal expenses.
- Damaged partner relationships.
Impact on Innovation Pipeline
IP breaches can stifle future innovation:
- Hesitancy to invest in groundbreaking R&D.
- Restrictive internal controls slowing development.
- Limited collaboration due to exposure fears.
- Overly cautious partnership approaches.
This chilling effect is a damaging long-term consequence.
Learning from Case Studies
Analyzing breaches reveals patterns. Effective strategies incorporate these lessons by:
- Identifying similar vulnerabilities internally.
- Implementing targeted protection for high-value IP.
- Creating response plans based on breach patterns.
- Conducting regular breach scenario simulations.
Studying others’ failures helps build resilient IP protection proactively.
Prevention Strategies and Best Practices
Protecting IP requires a multi-layered approach: technical, human, and legal.
Establishing Comprehensive IP Policies
Start with clear policies defining ownership, usage rights, and security protocols:
- Documentation Standards: Ensure proper attribution and ownership records.
- Classification Systems: Identify sensitivity levels for IP assets.
- Access Control Guidelines: Implement the principle of least privilege. Learn about controlling document access.
- Onboarding/Offboarding Procedures: Emphasize IP protection responsibilities.
Technical Safeguards Against IP Leakage
Implement technical controls to reduce breach risk:
- Data Loss Prevention (DLP): Monitor and control information transfers.
- Digital Rights Management (DRM): Maintain control over shared documents. Papersend offers robust document protection.
- Secure Development Environments: Use strict code repository access.
- Encryption: Protect data at rest and in transit.
Specialized tools monitoring code repositories can provide early warnings of potential theft.
Employee Education and Awareness
Your workforce is key. Effective training should:
- Explain what IP is and why protection matters.
- Provide specific examples of proper/improper handling.
- Outline consequences of breaches (individual and company).
- Establish clear reporting channels for security issues.
Regular training turns employees into active security partners.
Legal Protections and Enforcement
Strong legal frameworks back up technical and policy measures:
- Non-Disclosure Agreements (NDAs): For employees, contractors, partners.
- Employment Contracts: With clear IP ownership clauses.
- IP Registrations: Timely patents, trademarks, copyrights.
- Licensing Agreements: Explicit terms for permitted IP use.
These instruments establish rights and deter theft.
Third-Party Risk Management
Extend protection to your ecosystem:
- Security Assessments: Thoroughly vet third parties before granting IP access.
- Contractual Requirements: Include security obligations with verification.
- Limited Access Protocols: Restrict exposure to essential information only.
- Regular Audits: Conduct compliance and security reassessments.
This comprehensive approach significantly reduces vulnerability to accidental loss and deliberate IP theft.
Reacting to and Mitigating Damage
Despite prevention, breaches can occur. A swift, well-executed response minimizes impact.
Immediate Response Actions
If a breach is suspected:
- Contain: Isolate affected systems/repositories immediately.
- Preserve: Document evidence using forensic techniques.
- Assemble: Convene the incident response team (Legal, IT, Security, Leadership).
- Assess: Conduct a preliminary analysis of the scope and nature.
Forensic Investigation
A thorough investigation should:
- Identify compromised IP assets.
- Determine breach methods and vectors.
- Establish a timeline of events.
- Assess if the attack was targeted or opportunistic.
This informs recovery and future prevention.
Legal Remediation Strategies
Legal action is often crucial:
- Cease and Desist Letters: To parties using compromised IP.
- Court Injunctions: To stop further use/distribution.
- Civil Litigation: To recover damages.
- Criminal Referrals: For violations of laws like the Economic Espionage Act.
Work with experienced IP legal counsel.
Reputation Management
Protect your reputation:
- Communicate transparently without causing panic.
- Clearly state steps being taken to address the breach.
- Reassure partners/clients about ongoing IP protection.
- Demonstrate implemented security improvements.
Proactive management can mitigate loss of confidence.
Learning and Improvement
Treat every breach as a learning opportunity:
- Analyze how the breach bypassed existing protections.
- Identify security gaps and weaknesses.
- Develop specific improvements.
- Update training based on lessons learned.
This continuous improvement cycle strengthens overall IP security. Preparing response capabilities beforehand is crucial.
Secure Your Innovations with Papersend
In a world where intellectual property leakage can silently erode your competitive edge, ensuring your proprietary documents remain secure isn’t just important—it’s essential. As discussed, internal threats and digital vulnerabilities are major culprits. Protecting your trade secrets requires proactive, robust measures.
Imagine confidently sharing critical documents using a platform that gives you complete control and insight. Papersend’s advanced secure document sharing and Virtual Data Rooms offer powerful protection against unauthorized access and sharing, backed by detailed document tracking. Safeguard your innovations and gain peace of mind.
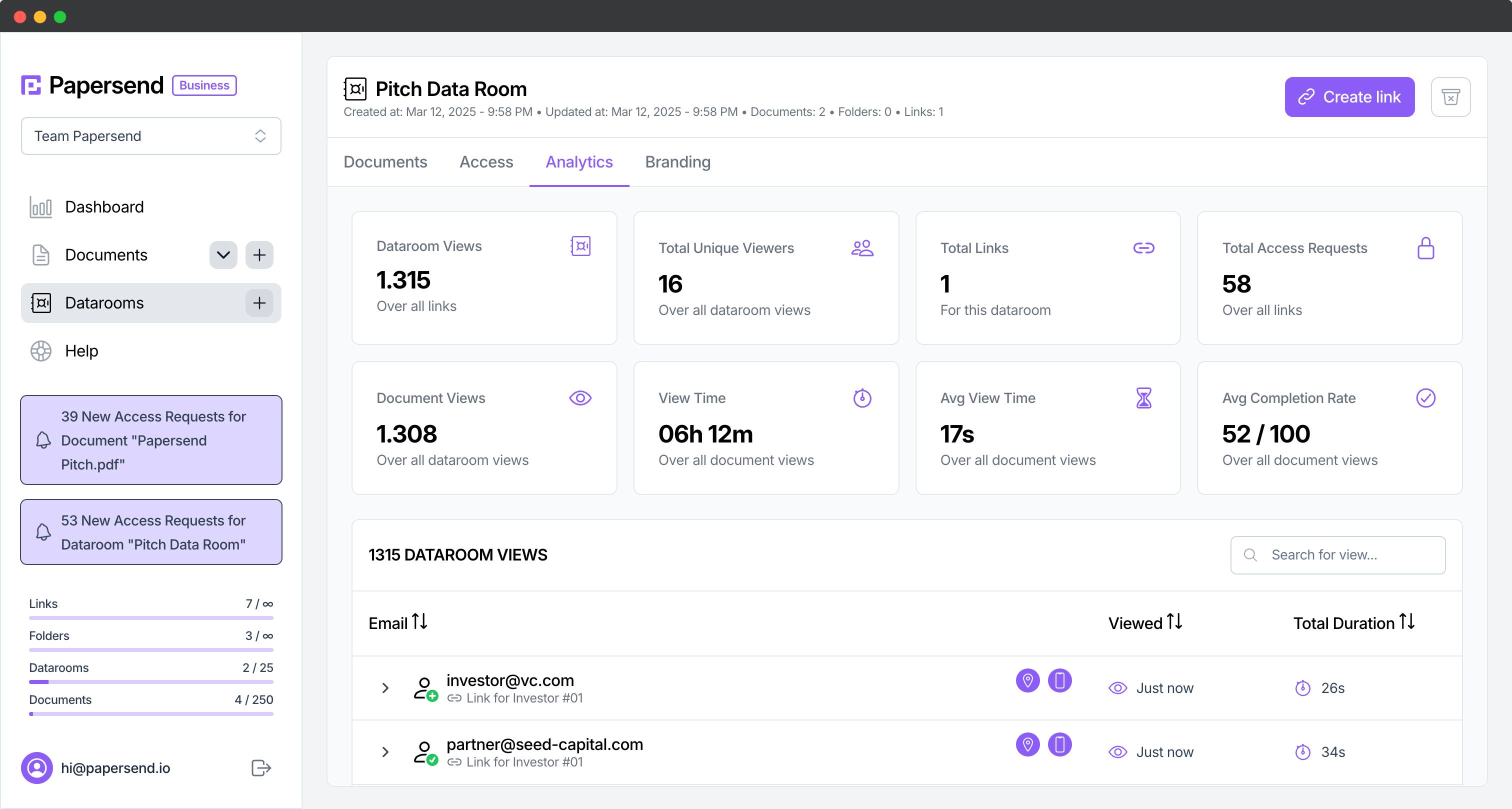
Don’t leave your most valuable assets vulnerable. Explore how Papersend shields sensitive information from internal and external threats, turning document sharing into a secure, controlled process.
Frequently Asked Questions
Intellectual property leakage refers to the unauthorized departure of valuable intellectual property assets, such as trade secrets or proprietary information, from an organization. Unlike outright theft, it often occurs gradually and sometimes unintentionally, making robust secure document sharing practices crucial.
Common causes include internal threats (departing or careless employees), digital vulnerabilities (unsecured systems, weak access controls), third-party exposure, and inadequate legal protections. Many breaches stem from poor document access control.
Implement comprehensive IP policies, use technical safeguards like encryption, Data Loss Prevention (DLP), and secure platforms like Papersend for document protection. Ensure strong legal frameworks (NDAs, contracts) and educate employees.
Immediately contain the potential breach by isolating systems, preserve all evidence meticulously, assemble your incident response team (legal, IT, security), and conduct a thorough forensic investigation to understand the scope and impact.
Secure document sharing platforms like Papersend provide granular access controls, download prevention, watermarking, and detailed document tracking. This helps ensure only authorized individuals access sensitive IP and provides an audit trail, reducing leakage risks.
Employees often have legitimate access to sensitive information. Leakage can occur accidentally (e.g., mishandling data) or intentionally (e.g., taking data when leaving). Robust offboarding procedures and continuous training are key defenses.