Essential Data Room Security: A Best Practices Guide
Why Robust Data Room Security is Non-Negotiable
In today’s digital landscape, protecting sensitive information during critical business processes has never been more important. Data room security forms the backbone of confidential document sharing, whether you’re engaged in M&A transactions, fundraising, or legal proceedings. Implementing robust security measures in your virtual data room ensures your organization’s most valuable information remains protected while maintaining necessary accessibility.
Implementing Multi-layered Access Controls
A secure virtual data room begins with sophisticated access management. Rather than simple username/password combinations, modern data rooms employ multi-factor authentication (MFA) that requires additional verification steps before granting access. This significantly reduces the risk of unauthorized entry even if credentials become compromised.
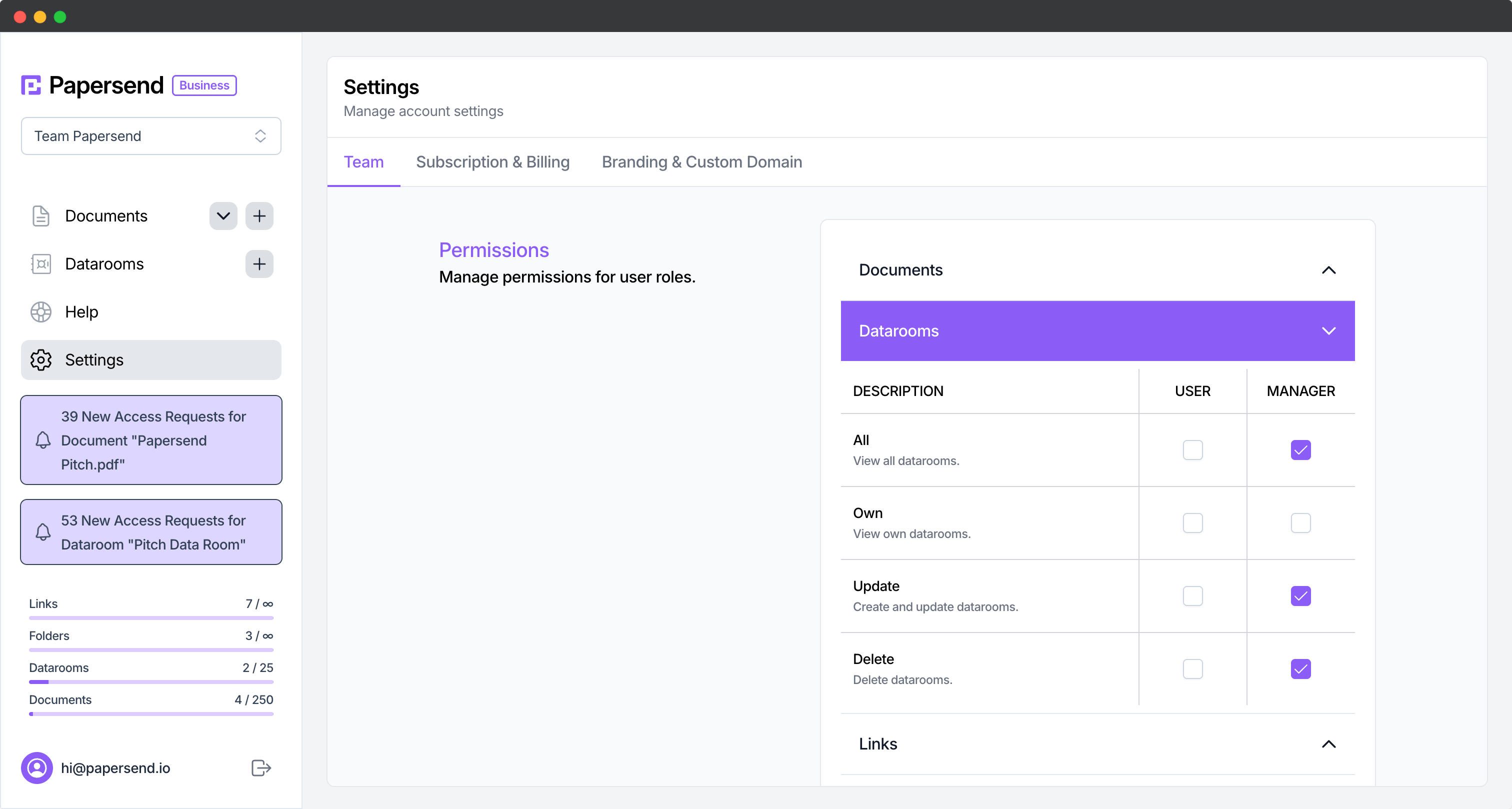
When configuring your online data room, implement role-based permissions that limit user access to only the documents they specifically need.
By creating distinct permission groups based on job function or information requirements, you establish information boundaries that prevent unnecessary exposure of sensitive data.
Document-level security features should also be utilized, including:
- View-only access that prevents downloading of sensitive files
- Watermarking documents with user identifiers
- Time-limited access periods for temporary collaborators
- Detailed audit logs tracking all document interactions
Encryption and Data Protection Standards
Encryption serves as the foundation of data room security, transforming readable information into coded text that remains inaccessible without the proper decryption keys. Enterprise-grade virtual data rooms employ end-to-end encryption protecting data both in transit and at rest. This means information remains encrypted when stored on servers and while being transferred between users.
When selecting a secure data room provider, verify their adherence to established security standards and certifications. Look for providers compliant with SOC 2, ISO 27001, and GDPR regulations. These certifications demonstrate the provider’s commitment to maintaining rigorous security protocols and data handling practices.
Data residency considerations also play a critical role in maintaining compliance with regional regulations. Some industries and jurisdictions require data to remain within specific geographic boundaries. Ensure your virtual data room provider offers server locations that align with your compliance requirements.
Monitoring and Threat Prevention
Regular security monitoring forms an essential component of comprehensive data room security. Advanced virtual data rooms incorporate intrusion detection systems that identify suspicious activities in real-time. These systems can alert administrators to potential threats before they escalate into security breaches.
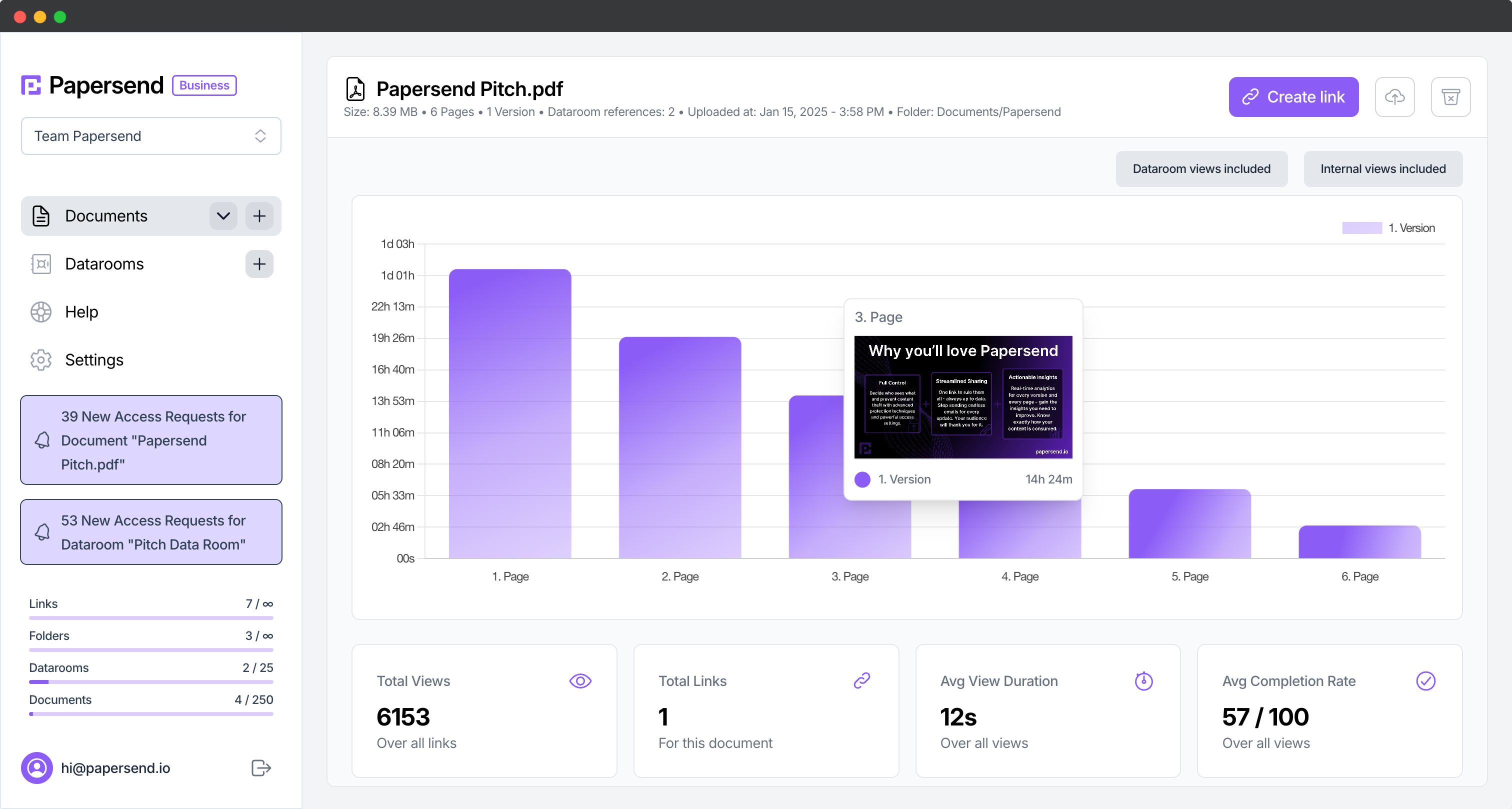
Implement a process for regular security audits of your data room environment. These reviews should examine user access patterns, permission configurations, and document activity logs to identify potential vulnerabilities or suspicious behaviors using features like document tracking. Schedule these reviews at consistent intervals and after significant organizational changes that might impact security requirements.
Data loss prevention (DLP) technologies help prevent unauthorized information sharing. These tools can identify attempts to download, print, or share protected documents outside established security parameters. By combining DLP with comprehensive audit trails, your organization maintains both preventative protection and the forensic capabilities necessary to investigate any security incidents.
By implementing these essential data room security practices, you create a protected environment that balances accessibility with stringent protection measures. This approach ensures sensitive information remains secure throughout complex business processes while supporting necessary collaboration.
Key Takeaways
| Takeaway | Explanation |
|---|---|
| Multi-layered Access Controls | Employ multi-factor authentication and granular, role-based permissions to secure data rooms and minimize unauthorized access risks. |
| Regular Monitoring & Audits | Conduct routine audits and establish robust monitoring systems (like detailed activity logs) to detect suspicious activities and ensure compliance. |
| Strong Encryption Standards | Ensure your provider uses end-to-end encryption (e.g., AES-256) and complies with security standards like SOC 2 and ISO 27001 for data protection. |
| Address Human Factors | Implement training programs to raise awareness of security best practices and reduce risks associated with human error and potential insider threats. |
| Comprehensive Compliance Framework | Develop an integrated compliance strategy addressing relevant regulations (GDPR, HIPAA, etc.) to ensure your data room meets necessary legal protections. |
Identifying Key Security Vulnerabilities
Even the most sophisticated virtual data room can be compromised if you fail to identify and address common security vulnerabilities. Understanding these potential weak points is essential for establishing comprehensive data room security protocols.
Access Control Vulnerabilities
Broken access control remains a prevalent security vulnerability. This occurs when users gain unauthorized access due to improper permission configurations.
Common access control vulnerabilities include excessive privileges, failure to revoke access promptly, inadequate segregation, and missing time-based restrictions. Regular permission audits are crucial.
Data Transmission Weaknesses
Inadequate encryption during data transfer can leave information vulnerable to interception. Secure virtual data rooms use end-to-end encryption, but verifying current standards is vital. Endpoint security (securing user devices) is equally important.
Human Error and Insider Threats
Human factors represent a significant vulnerability. Credential sharing, insecure downloads, phishing susceptibility, and permission misconfigurations are common risks. Mitigation involves strict authentication, clear policies, and regular security awareness training. Features like watermarking and audit logs enhance accountability.
Third-Party Integration Risks
Integrating data rooms with other tools can introduce vulnerabilities if not managed carefully. Assess third-party security practices, limit data sharing, and regularly review active integrations. Prioritize providers with secure API controls.
Addressing these key vulnerabilities creates a more resilient virtual data room environment.
Best Practices for Data Room Security
Implementing robust security requires a strategic approach balancing protection and usability.
Establish Comprehensive Access Policies
Define access policies based on document sensitivity and user roles. Implement the principle of least privilege, granting access only as needed. Use MFA, session timeouts, user groups, and approval workflows. Regularly review and update policies.
Secure Document Handling Protocols
Implement document-level controls like watermarking and view/download restrictions. Use view-only access for highly sensitive data and encrypted downloads when necessary. Utilize document versioning for integrity and audit trails.
Continuous Monitoring and Audit Procedures
Implement comprehensive logging of all user activities. Regularly review logs for unusual patterns. Conduct periodic security assessments covering user accounts, authentication, access controls, and integrations.
Training and Awareness
Develop training materials covering security expectations, phishing recognition, credential management, and secure document handling. Foster a security-conscious culture through regular awareness sessions and clear reporting channels.
Data Room Security Compliance Strategies
Meeting regulatory requirements (like GDPR, CCPA, HIPAA, SOX) is fundamental.
Understanding Key Regulatory Requirements
Identify applicable regulations based on industry, location, and data type. Recognize that compliance often involves meeting multiple standards simultaneously.
Developing a Compliance Framework
Create an integrated framework consolidating overlapping requirements. Map data types to regulations, implement standardized policies (retention, deletion, access requests, breach notification), and maintain detailed compliance records.
Implementing Technical Compliance Controls
Choose VDR providers offering built-in compliance features like data residency options, strong encryption, granular access controls, and DLP tools. Regularly audit these controls.
Building a Culture of Compliance
Integrate compliance into daily operations through role-specific training and clear accountability. Communicate expectations clearly to all users, including external partners. Prioritizing security and compliance builds trust.
Future Trends in Data Room Security
Staying ahead requires understanding emerging trends.
AI-Powered Security Enhancements
AI and machine learning enable sophisticated threat detection by analyzing user behavior and identifying anomalies. Future systems will offer predictive security measures.
Zero Trust Architecture Implementation
Operating on “never trust, always verify,” ZTA requires continuous verification, context-aware controls, micro-segmentation, and just-in-time access, reducing the risk surface.
Advanced Biometric Authentication
Beyond fingerprints, methods like behavioral biometrics and multi-layered authentication will provide stronger identity verification, combating password vulnerabilities.
Quantum-Resistant Encryption
Preparing for quantum computing threats, providers are exploring post-quantum cryptography to ensure long-term data confidentiality.
Blockchain-Based Audit Trails
Blockchain offers immutable, tamper-proof audit logs, providing verifiable records crucial for high-stakes transactions and regulatory compliance.
Staying informed about these trends ensures your data room solution remains robust against evolving threats.
Elevate Your Data Room Security with Papersend
Feeling overwhelmed by data breach threats and the complexity of securing sensitive documents? Effective data room security is essential, yet many organizations struggle with vulnerabilities like misconfigured access controls and inadequate monitoring.
With Papersend, gain peace of mind knowing your documents are protected by state-of-the-art security measures. Our secure document sharing platform provides:
- Multi-layered access controls: Utilize granular permissions and MFA for precise control.
- Advanced encryption: Keep data safe in transit and at rest.
- Robust tracking & analytics: Monitor engagement and detect anomalies with detailed logs.
Transform your document sharing experience and secure your most valuable information today.
Frequently Asked Questions
Implementing multi-layered access controls, using strong encryption standards like AES-256, regular security monitoring and audits, ensuring secure document handling protocols (like watermarking and download restrictions), and comprehensive user training are key best practices for robust data room security. Explore Papersend's features at https://papersend.io/.
Protect sensitive information by employing multi-factor authentication (MFA), granular role-based permissions, document-level security features (view-only, watermarking), end-to-end encryption, and conducting routine audits to maintain compliance and detect vulnerabilities within your virtual data room.
Encryption transforms readable information into coded text, making it inaccessible without the proper decryption keys. This protects data both in transit across networks and at rest on servers, ensuring that sensitive information remains confidential and secure from unauthorized access.
Multi-factor authentication (MFA) is a crucial security measure requiring users to provide multiple forms of verification (e.g., password + code from an app) before accessing the data room. This significantly reduces the risk of unauthorized access, even if one factor like a password is compromised. Papersend emphasizes strong security protocols.
Continuous monitoring involves tracking user activity, access logs, and system performance in real-time. This allows for the immediate detection of suspicious activities or potential threats, enabling swift response and mitigation before a significant breach occurs, thereby enhancing overall data room security. Learn about Papersend's tracking features.